As a Sys Admin when you are working with Linux systems, logs are very important to investigate the root cause and troubleshoot the issues when an incident occurs. In a Linux system, you can find various types of logs such as system logs, application/service logs, hardware-related logs and etc. Those logs contain information about all the events for a service which includes Errors, Warnings, and Informational messages. But when you are storing those logs in the same server, you have to address the data protection of it, if you are maintaining a compliance requirement in your organization. Because some application-related logs will contain sensitive information or PII (Personally Identifiable Information) inside it.
In this article, I will show you how to protect log files by encrypting logs and managing them using Linux built-in tools like GNU Privacy Guard (aka GnuPG/GPG) and logrotate utilities.
Why Encrypt Logs?
There are several reasons why logs are often encrypted and stored:
As I mentioned earlier, most of the application logs, database query logs, and systems audit logs may contain sensitive or PII about a system, its users (who accessing the system), and their activities. Here are some examples of sensitive information that could be contained in log files:
- Personal information: Names, addresses, and phone numbers of users.
- Login credentials: Usernames and passwords/hashes, that could be used to gain unauthorized access to a system.
- Financial information: Credit card numbers or bank account numbers, if they are processed or stored by the system.
- Confidential business information: Trade secrets or proprietary data, if the system is used for business purposes.
- Private communications: Emails or chat messages, if the system is used for communication purposes.
Therefore it’s important to be aware of the potential sensitivity of log files and to handle them with care to protect the privacy and security of individuals and organizations.
Next, as compliance, some organizations have regulations that require logs to be encrypted and stored in a secure manner to ensure the privacy and security of customer data (Ex: GDPR requirements).
Also in the event that an attacker captures a machine with sensitive logs, we need to guarantee that he will gain little or no information from the log files. The attacker’s only option will be to delete the log file, which is a very noticeable action.
So, you can absolutely run the log encryption process separately via the cron tab or some other way. But this would be an extra step with error-prone. You can actually use logrotate utility to directly handle encryption which gives you more flexibility to manipulate the logs in the Linux servers.
Why Log Rotation?
In any Linux distribution, most of the logs are stored in a reserved location called /var/log directory and these log files keep on growing in size over a period of time. For a busy server, log files may grow quickly into very large sizes. This will cause your server to run out of disk space quickly. Besides, opening a single larger log file for inspection will cause a freeze in your terminal sometimes.
As a solution to the disk space running out, you can review the logs inside the /var/log directory and do a disk cleanup process by deleting the old logs. But that is a kind of a toiling task when it comes to a larger Linux server environment. So to save your time from manual tasks you can automate log management using logrotate utility.
What is Logrotate?
In short, it’s an automated log management tool built in with Linux systems and it is an easy-to-use sysadmin tool that manages large numbers of log files. As the name implies, this tool helps us to split large size of log files into smaller chunks of log files, compression or archive the old logs, delete them after a certain number of logs have been reached (to free up disk space) depending on their size, date or exceeds a certain limit which configured in the logrotate configurations.
This utility can be run every day, weekly, monthly, or as per the size of the logs and also can be customized on a per-directory or per-log basis. Once you configured it, this process is fully automated using logrotate without any further need for human interaction.
Simply the log rotation process renames a current log file. For example, the existing syslog.log becomes syslog.log.1, and a new syslog.log log file is created for new log entries. Older log files are compressed and appear as syslog.log.2.gz, syslog.log.3.gz, syslog.log.4.gz, and so on.
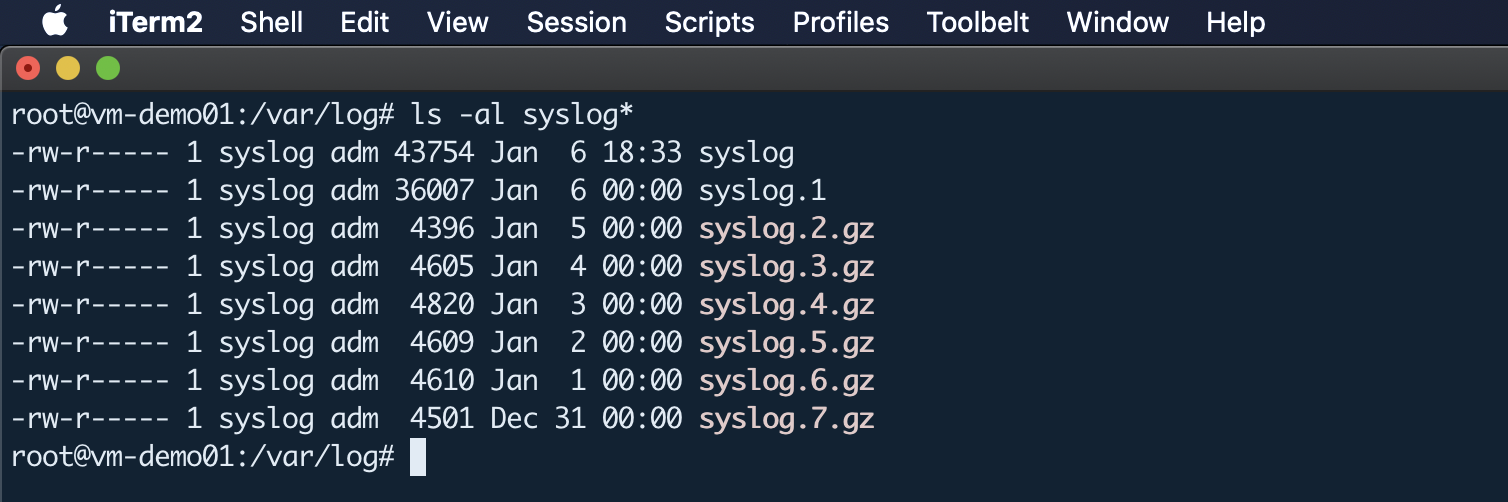
Let’s walk through the installations and configurations of GPG and Logrotate as per your requirement.
Install and Configure GnuPG
GnuPG is just another computer program that provides digital encryption and signing services using the OpenPGP standard.
Install GnuPG
This GnuPG tool already ships with the latest Linux distributions. If it is not present, you can install it by using the following command.
apt install gnupg
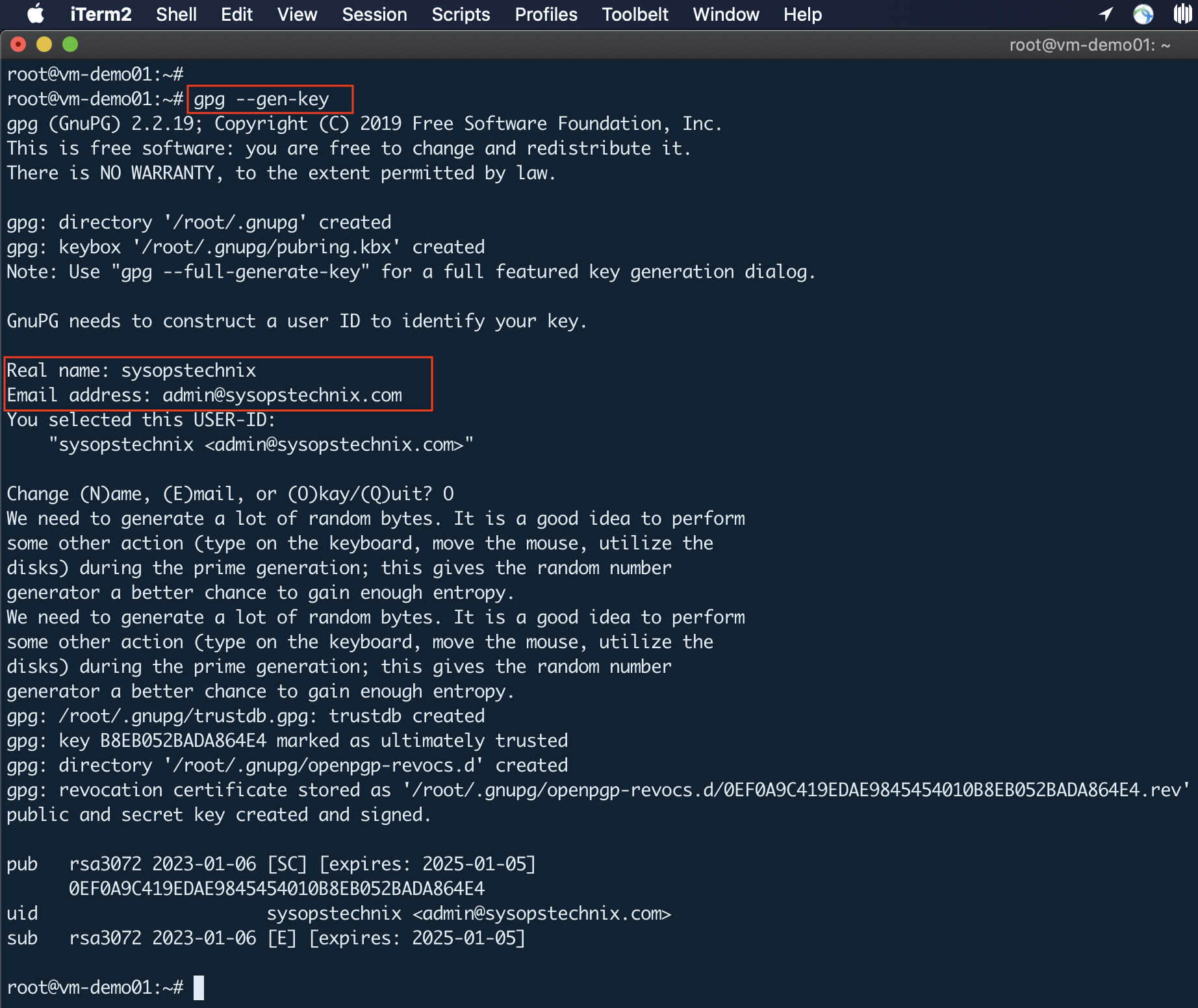
Genarate a GPG Key Pair
After the successful installation of gpg, you can move forward to generate a gpg key pair. The gpg keypair will have a public and private key. The public key is sharable with the individuals you want to view and access your files or data encrypted with the private key.
gpg --gen-key
Execution of the above-mentioned command will store some information on your system which includes your real name and email address. After you have confirmed that the entered information is correct, gpg command will generate a key pair: a public and private key, a fingerprint of the user, and a revocation certificate:
During the key generation process, you will get a prompt to enter a passphrase to protect the generated key.
As a best security practice, you shouldn’t be keeping your private key on the same server. Therefore, generate the key pair on a separate secured machine and extract the public key. Then import that public key to your server where you need to do the encryption.
Export Public Key
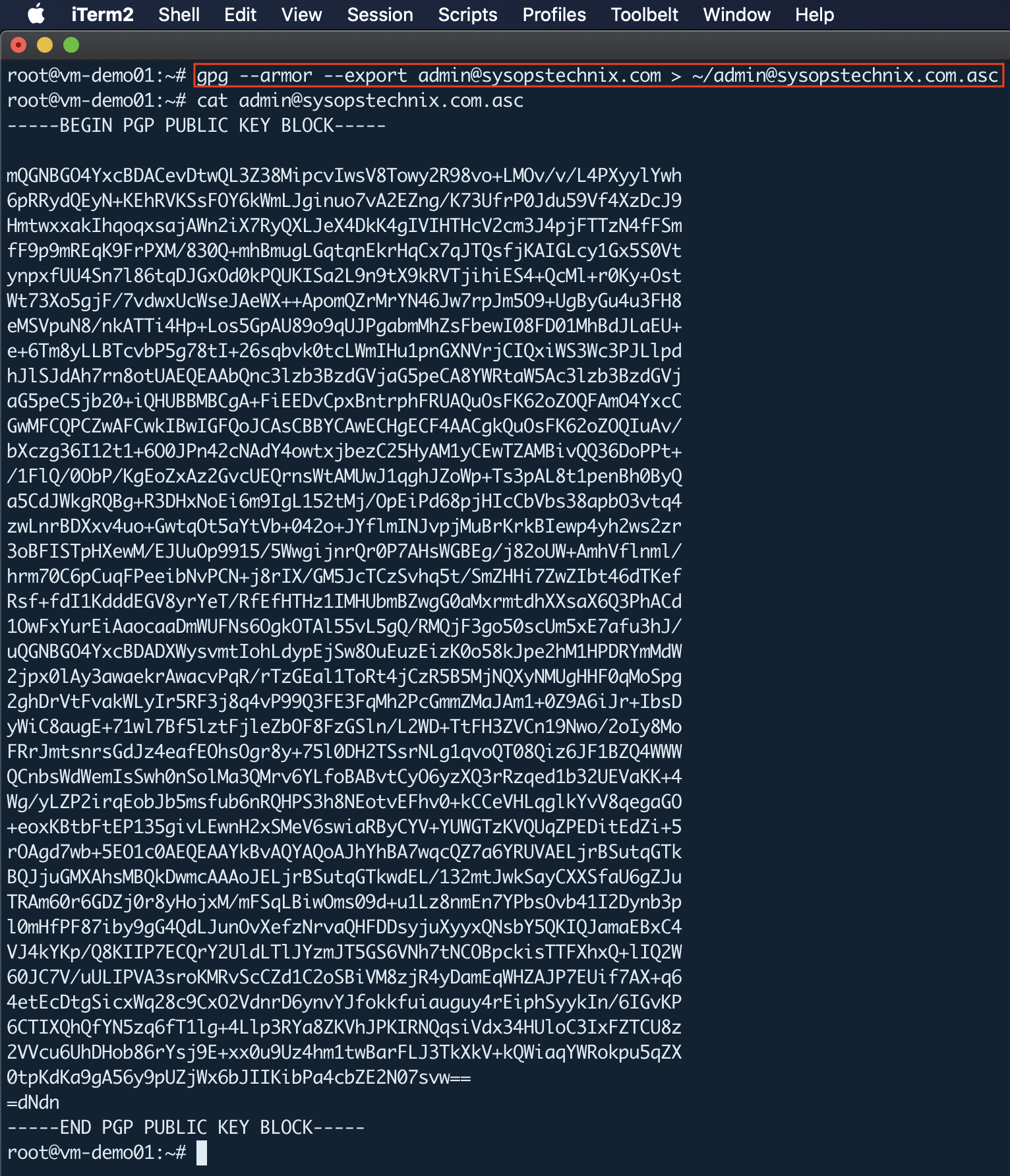
Using the following command you can extract the public key.
gpg --armor --export [email protected] > ~/[email protected]
Once you export the GPG public key, you can see it like this:
Import Public Key to Your Server
Then move to the server where you want to encrypt logs and import the key using the following command.
# Move the public key to the intended server and import it
gpg --import ~/[email protected]
Try Encryption and Decryption
Once you generated the key pair, you can try following commands for encryption and decryption.
#Encrypting a file
gpg --encrypt --recipient sysopstechnix access.log
#Decrypting a File
gpg --decrypt access.log.gpg > access.log
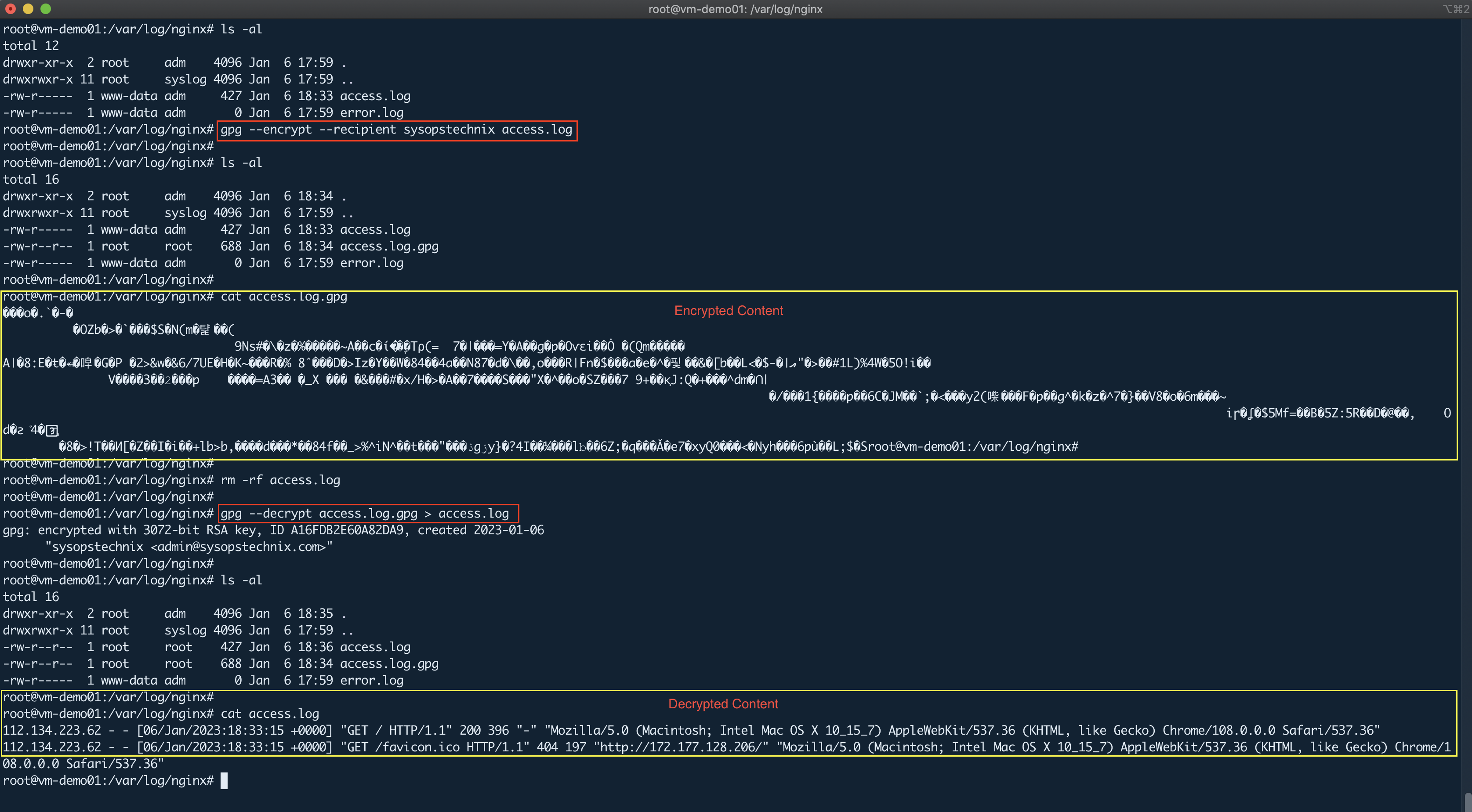
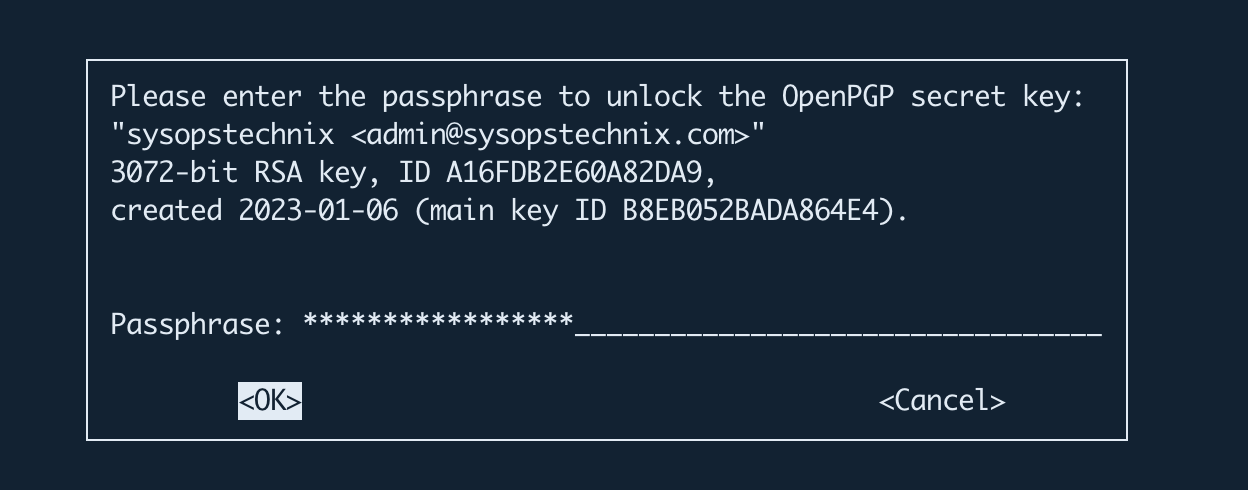
Note that when you decrypt the file, you will get a prompt to enter the passphrase that you gave in the key generation process.
Install and Configure Logrotate
Install Logrotate
The logrotate utility is typically installed by default on major Linux distros. If it is not present, you can install it using the following command.
apt install logrotate
The logrotate utility main configurations can be found in the /etc/logrotate.conf file and it has the default settings. In this case, there is no modification is needed to do in the main configuration file. So if you need to configure application-specific configurations, you can create a separate file inside the /etc/logrotate.d/ directory.
Usually, when a package is installed on the system, they drop the log rotation configuration file in /etc/logrotate.d/ directory. Here I have already installed the Nginx server and I’m using its default logrotate configuration file (/etc/logrotate.d/nginx) for the modifications accordingly.
Create a Sample logrotate Configuration File
Let’s assume that we need to set the log files to rotate on a daily basis on the Nginx server and keep the 14days log files in an encrypted manner.
Please Note: If you have multiple log files ‘/var/log/nginx/*.log’ in one directory, you can add them all with the wildcard option. Also, you can mention multiple log file locations that required the same configuration as follows.
/var/log/nginx/*.log
/var/log/nginx/sysopstechnix.com/*.log {
daily
missingok
rotate 14
compress
delaycompress
notifempty
create 0640 www-data adm
sharedscripts
compresscmd /usr/bin/gpg
compressoptions --encrypt --recipient "sysopstechnix"
compressext .gpg
dateext
prerotate
if [ -d /etc/logrotate.d/httpd-prerotate ]; then \
run-parts /etc/logrotate.d/httpd-prerotate; \
fi \
endscript
postrotate
invoke-rc.d nginx rotate >/dev/null 2>&1
endscript
}
According to the above script configurations, the following 3 lines are added to the default Nginx logrotate file. Those 3 lines simply override the default gzip compression method with the GnuPG utility and do the encryption process.
compresscmd /usr/bin/gpg
compressoptions --encrypt --recipient "sysopstechnix"
compressext .gpg
Contents of logrotate Configuration File
Let’s understand each directive specified in the above configuration file.
- daily: Log files are rotated every day.
- missingok: If the log file is missing, go on to the next one without issuing an error message.
- rotate 14: The number of files to be rotated before being removed.
- compress: Older/rotated files to be compressed.
- delaycompress: Do not compress the current log and last rotated log.
- notifempty: Don’t rotate the file if it is empty.
- create 0640 www-data adm: After rotation create an empty log file with permission specified.
- sharedscripts: The sharedscripts means that the postrotate script will only be run once (after the old logs have been compressed), not once for each log which is rotated.
- compresscmd: Specifies which command to use to compress log files.
- compressoptions: Command line options may be passed to the compression program, if one is in use.
- compressext: Specifies which extension to use on compressed logfiles, if compression is enabled.
- dateext: Append the date to rotated file names.
- prerotate/endscript: The lines between prerotate and endscript are executed before the log file is rotated and only if the log will actually be rotated.
- postrotate/endscript: The lines between postrotate and endscript are executed after the log file is rotated.
There are many other options available that can be used. I have listed here only frequently used ones. A detailed list can be obtained on the man page of logrotate.
man logrotate
That’s it, so you can encrypt logs in other applications like this using logrotate + GnuPG tools.
Testing & Troubleshooting
Dry run
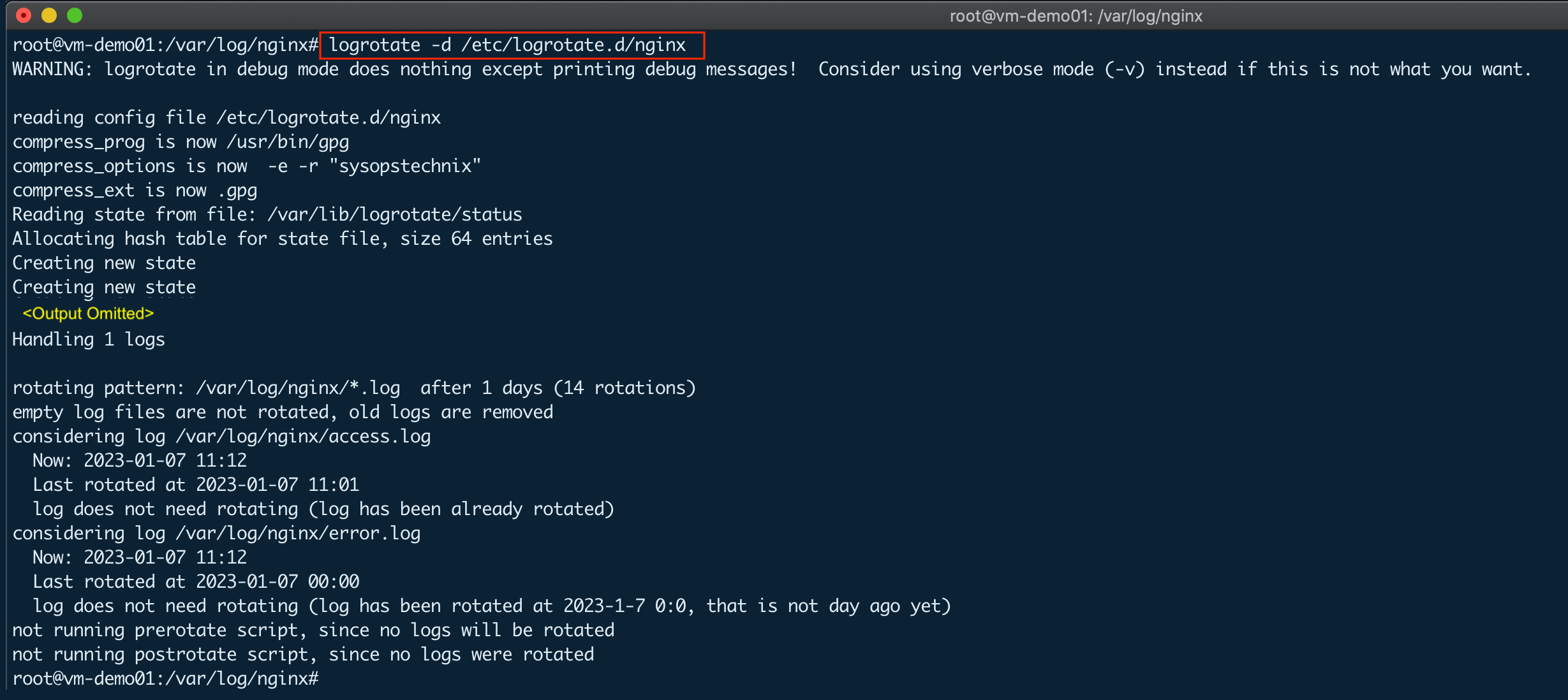
We will dry-run the above config file to check how it will work in the actual run. -d option dry runs utility but doesn’t rotate logs in actual.
logrotate -d /etc/logrotate.d/nginx
Running logrotate Manually
#Invoke logrotate on all logs as configured in /etc/logrotate.d/*:
logrotate /etc/logrotate.conf
#Invoke logrotate for a specific configuration:
logrotate /etc/logrotate.d/nginx
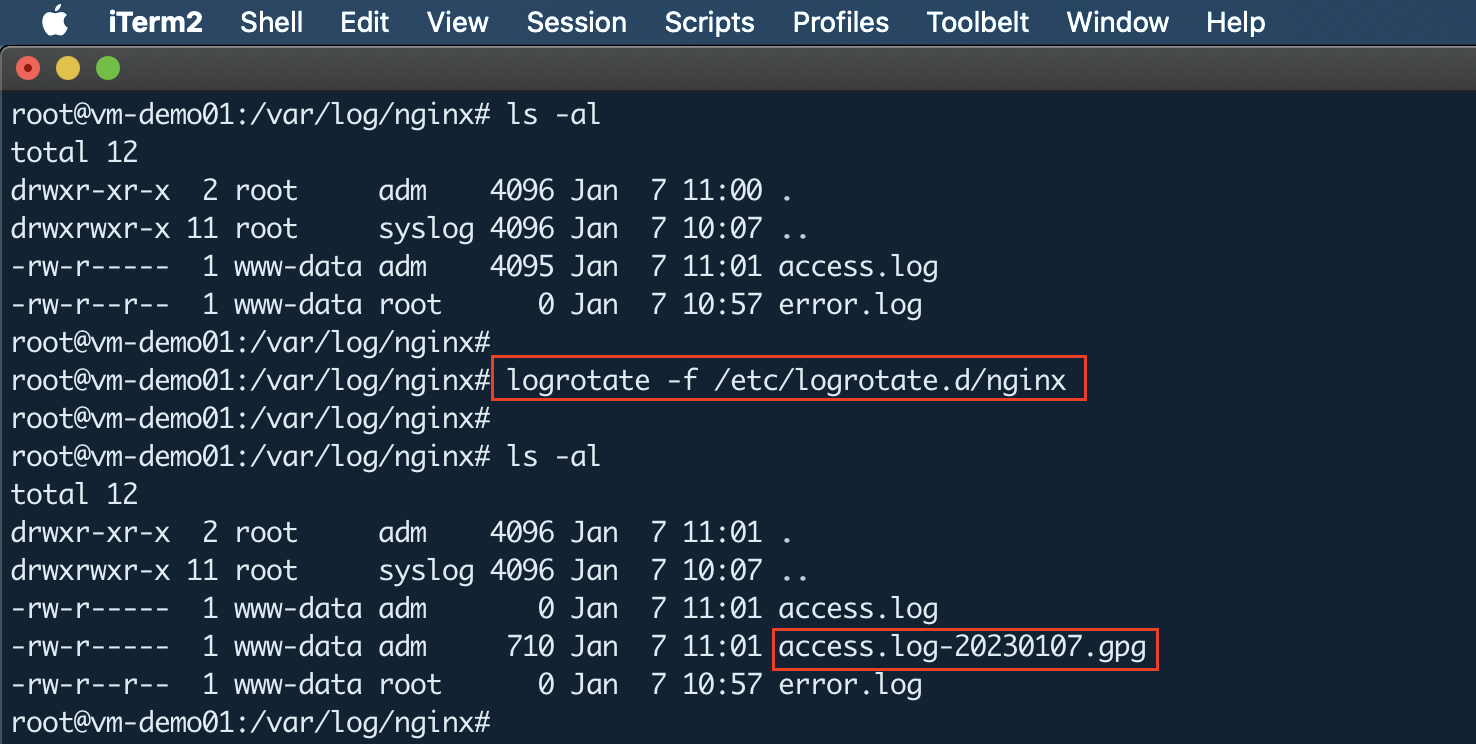
#We can force logrotate to rotate log files even when rotation conditions are not met, by using -f option.
logrotate -f /etc/logrotate.d/nginx
After manually running the Nginx logrotate configuration with the force option, you can see log files are encrypted with the .gpg extension as follows.
Logrotate Cron Job
The cron job is needed for logrotate and it should automatically be created during installation under /etc/cron.daily/ directory. By default, the log rotation process would run once a day. But if you want to run the process hourly, you would need to copy /etc/cron.daily/logrotate into /etc/cron.hourly/ directory. Also, in your logrotate config file, you would also need to specify hourly with the desired retention period.
Conclusion
To sum up, logrotate is a very useful utility pre-built-in with the latest Linux distributions that provide a lot of features to simplify the sys admin’s tasks. Additionally, with the integration of the GnuPG digital encryption service, we can meet the organization’s compliance requirements related to data protection when storing log files on Linux servers.
If you found this article helpful, please share with your friends and spread the knowledge. Please feel free to comment below if you have any queries/concerns. We will get back to you as soon as we can :).

